Today’s world operates in real-time. Similarly, the workforce has evolved into being mostly remote while consumers continue to engage on-demand and online. With the world’s population participating in online processes now more than ever, protecting personal and business data requires vigilance, the latest technology, and a well-crafted plan for discovering, analyzing, and maintaining information security compliance.
Information security prevents data risks and threats.
Data exposure can lead to higher costs, legal risks, and damaged reputations. Organizations of all sizes must safeguard confidential digital and printed data from illegal access, public exposure, and modification without authorization.
However, as organizations grow, so too does the security vendor portfolio.
Recent market intelligence reports that:
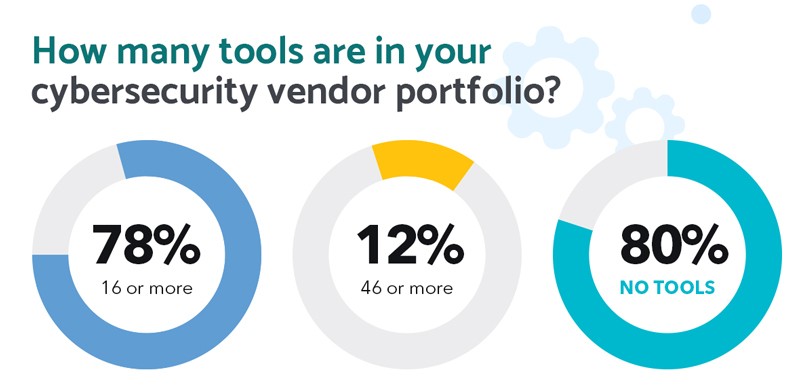
- 78% of Chief Information Security Officers (CISOs) have 16 or more tools in their cybersecurity vendor portfolio.
- 12% of CISOs have 46 or more tools.
- 80% of organizations are interested in consolidating security vendor portfolios.
An effective information security plan considers all vendor tools and, whenever possible, consolidates technology for cost reduction. Reinforcing data protection for today’s on-demand environments requires assistance from information security experts.
Prakat’s Data Security experts identify the latest vulnerabilities and risks while engineering solutions for data lifecycle protection in centralized and distributed environments. During the data discovery process, Prakat creates a logical tracing map by scanning across all layers of the network where data is stored (emails, databases, servers, logs, and index locations among others).

Analysis of scanned enterprise-level data generates a data risk profile, a mitigation plan for risk management, and data protection strategies. A compliant information security solution adheres to ever-changing regulatory requirements. Assessment audits, due diligence, and risk mitigation are required for a compliant solution to manage, implement, improve, and ensure secure data access. Prakat delivers solutions that prevent downtime, increase agility, and maximize data flow efficiency securely in both physical and virtual environments.
Stop security threats before they happen with Prakat Solutions. Contact us today to learn more!
Connect with Prakat.
![]()
A true security solution that stops threats before they happen.
Connect with Prakat.
![]()